The threat to the cold chain from cybercrime is growing and operators should be prepared, writes Nick Hughes.
When M&S and the Co-op fell victim to cyber attacks in the spring of this year there was no hiding place for the retailers. Pictures of empty Co-op shelves soon started circulating on social media while M&S was forced to stop taking online clothing orders for several weeks after its servers were encrypted by hackers. M&S is expected to take a £300m financial hit from the attack and also faces the threat of class action lawsuits from customers affected by the loss of their private data.
The high-profile incidents should serve as a warning of how cybercrime is a growing danger for all businesses, including those operating within the cold chain. The distributor Peter Green Chilled recently fell victim to an attack which impacted the supply of products, including chilled meats, to a number of food retailers. One of the company’s customers, Wilfred Emmanuel-Jones, founder of The Black Farmer food range, told The Telegraph the incident had left his business in a “desperate situation” with 18 pallets of Swedish meatballs stuck in limbo and at risk of being thrown away.
The attack on Peter Green Chilled is far from an isolated case. Cold Chain Federation chief executive Phil Pluck says he knows of around 10 attacks or attempted attacks impacting member companies during the past 18 months alone. The actual number is likely to be even higher given the reluctance of businesses to admit to a breach of their security.
The director of a cold chain logistics company, which was the victim of a cyber-attack a few years ago, says that when he started talking openly about the attack in its aftermath he was surprised at how many peers had suffered the same fate. “It’s a lot more prevalent than people realise,” he says.
Vulnerable system
The spate of attacks has cast a spotlight on the vulnerability of the UK’s food system to cyber attacks and trained the minds of businesses on what can be done to protect it. The UK operates a highly efficient, centralised system of food supply chain management that relies on real-time inventory management, temperature control and rapid distribution. When it runs smoothly, the system is hugely effective at ensuring products are in the right place at the right time, but its efficiency can become a vulnerability when one part of the chain is disrupted – as proven by those pictures of empty retail shelves. Hackers are well aware of this and “have made no secret of the fact that the food supply chain is one they would
particularly want to target”, says Pluck.
“A lot of people believe that cyber incidents or cyber security is just the responsibility of the IT team. It’s not”
The most common attacks are so-called ransomware attacks where hackers encrypt a victim’s data and lock them out of computer systems, demanding payment to hand back control. Without access to critical IT infrastructure, like warehouse management systems, businesses face not knowing what stock they hold, where it needs to go or where their trucks are at a particular point in time. This effectively disables the entire logistics operation, impacting availability of stock and ultimately costing sales.
Besides the direct operational disruption caused by an attack, businesses face dealing with multiple ripple effects. One of the biggest risks is of wasted stock, explains Gordon Smith, lead security consultant at Citation Cyber. “Because there are such short turnarounds for refrigerated goods, if they end up sitting
in a warehouse and you can’t deliver them they’re going to go bad and end up getting binned [so] there’s huge food waste that comes off the back of an attack,” Smith says.
Additionally, Pluck points out that logistics providers that store and transport temperature controlled foods don’t actually own any of the stock. “Not only are you losing business, you are potentially losing upwards of £2m of stock each day because it belongs to someone else [and] you are responsible for it,” he says. Cyber insurance policies can mitigate some of the financial risk to companies (see column to the right) but the reputational damage caused by an attack can take longer to repair.
“A key focus should be on keeping software up-to-date including regular patching and vulnerability scanning”
Sophisticated attacks
Cyber attacks are becoming more sophisticated and thus more difficult to detect with hackers often seeking to gain access to a company’s systems via third party suppliers or IT service providers. The integrated nature of food supply chains means suppliers and their customers will invariably have common IT systems that allows logistics partners to talk to one another. This means that an attack on one part of the chain potentially exposes the rest of the chain to the same threat. “If suppliers have vulnerabilities which are exploited by a threat actor, they may gain access to that supplier’s system to deploy malware onto their software, which is then distributed to retailers when they update or download software from that supplier,” explains Serena France-Hayhurst, placement leader for cyber, media & technology practice at insurance broker Marsh during a recent Cold Chain Federation webinar on cybercrime.
Most cyber attacks are financially motivated but Smith says there is also a growing threat from state-sponsored attacks on critical infrastructure. Food falls firmly into this category. In a recent report for the National Preparedness Commission titled ‘Just in Case: 7 steps to narrow the UK civil food resilience gap’, Tim Lang, Professor Emeritus of food policy at City St George’s, University of London, identified economic threats from cyber insecurity, ransomware and technology as “an issue that has rocketed up the agri-food agenda”.
Lang argued that “food is and should remain a significant sector for cyber security care” due to the potential food system impacts. In a scenario where multiple food distributors were targeted in a systematic way the result could be total supply chain paralysis. “If you knock out the shipping containers or harbours or warehouses where the foods go […] the entire chain will stop,” warns Smith at Citation Cyber. This can lead to food shortages, panic buying and, in a worst-case scenario, civil unrest and disorder.
Although businesses are becoming wise to the threat from cybercrime, they can still be taken by surprise. “We thought we were quite well versed in all things cyber. We thought we understood it. We put all the precautions in place. We did everything we thought necessary to avoid it, and how wrong were we,” says the director of the logistics company who spoke to us for this article. The attack left the business locked out of its warehouse management systems for several days.
Experts say organisations like the National Crime Agency will almost always recommend that businesses don’t pay the ransom. Indeed, company directors run the risk of being prosecuted should evidence show that the proceeds from the ransom are being used to fund terrorist organisations. Yet when the only viable alternative is to rebuild IT systems from scratch, as M&S has reportedly done, it’s perhaps no surprise that some businesses choose to bow to the hackers’ demands.
Response plan
Smith says that as part of a company’s strategy for dealing with a security breach it’s vital to have developed a cyber incident response plan that simulates how you would respond in the event of a ransomware attack. That includes determining who is going to make the decision over paying the ransom. He stresses the plan should involve the entire organisation, not just the IT department. “A lot of people believe that cyber incidents or cyber security is just the responsibility of the IT team. It’s not. You’ve got legal requirements around it, such as contacting the ICO (Information Commissioner’s Office) for any kind of data breach. You’d have PR and marketing teams potentially writing press releases out to the public. You have HR potentially involved because if your payment systems go down you still need to pay all your employees. So a cyber incident does involve every single element of the company, and that cyber incident response plan dictates how the company should act.”
For companies developing a cyber security strategy from scratch, the first thing Smith advises is to conduct a cyber risk assessment to identify where the risks in the organisation exist – from internal IT systems to third party suppliers and individual users. From here, companies can then start creating
a list of priorities to work through.
A key focus should be on keeping software up-to-date including regular patching and vulnerability scanning. Multi-factor authentication for systems, applications and email accounts can provide another layer of security, while Smith urges businesses to maintain off site backups of all their data which can help speed up recovery from an attack.
Businesses also need to invest in cyber security training for employees that includes ‘how to’ guidance on issues like identifying phishing scams, creating strong passwords and handling sensitive data. “Users are always the weakest link around a cyber security strategy,” Smith suggests. “That user awareness piece is a huge element [of cyber security].”
“The cold chain’s efficiency can become a vulnerability when one part of the chain is disrupted”
Government support
Following the attack, the logistics company that spoke to us employed specialists to audit its systems and help put in place extra protections. “We thought we had good controls in place. After this experience we quickly learned there was so much more we could and would do,” says the director.
Yet he still feels businesses lack support from the authorities on how to prevent an attack and deal with the fallout when one occurs. “Although there’s growing awareness of cyber[crime] there’s still a lack of understanding about what people need to do. The support isn’t really there. There’s no road map,” he says.
Pluck agrees that there is very little guidance for businesses facing cyber threats – something that needs to be addressed as the risk from hackers grows ever greater. He also wants to see the UK government acknowledge the importance of the cold chain, through which 50% of the nation’s food travels, by giving it Critical National Infrastructure (CNI) status. “We have around 460 very specialised warehouses containing the food that feeds the nation, and they also contain critical medicines,” says Pluck. “What I’m saying to the government is we don’t need your money, but what we do need is to work with you to create a crisis recovery plan for our industry.”
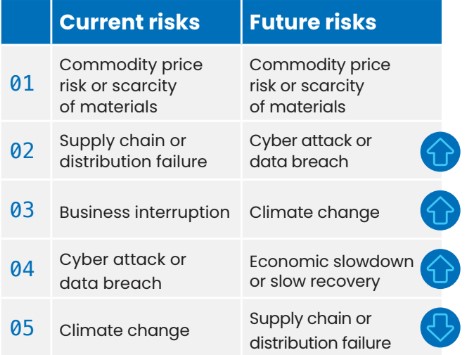
THE CHANGING FACE OF RISK
Top five risks facing food, agribusiness and beverage organisations (according to Aon Global Risk Management Survey, 2023)
INSURANCE AGAINST CYBERCRIME
As the threat from cybercrime grows ever greater, more and more companies are looking to protect themselves against the financial risk of business interruption by investing in a cyber insurance policy.
“The cyber insurance will essentially look to help clients have cover where they may have a loss of income or they’ve had to incur increased costs during that time that they are down as a result of the cyber attack,” says Serena France-Hayhurst, placement leader for cyber, media & technology practice at
insurance broker Marsh.
Cyber insurance exists on a spectrum and France-Hayhurst stresses the importance of businesses checking to see what is covered under their specific policy. Some policies are broad enough to cover situations where IT providers or critical suppliers suffer an outage that impacts the insured business.
Insurance may also extend to covering extortion expenses where the business under attack has decided to pay a ransom demand to regain access to its systems.
Some policies also cover incident response expenses – the costs a company incurs when bringing in external help to help mitigate the impact of the incident such as experts in digital forensics and crisis and reputation management.
Third party liability cover can also be secured where sensitive data has been compromised following an attack.
More than just acting as underwriters, France-Hayhurst explains that insurers like Marsh can also call on in-house expertise to help businesses understand their cyber risk profile and work with them to improve their security.